 If you run a family office, you already know the feeling. A perfectly reasonable decision in one corner of the operation can create a problem in another. A private deal looks fine on paper, then liquidity gets tight because capital calls do not wait for your timing. A wire request lands late on a Friday, the right approver is traveling, and the process that usually feels smooth suddenly has sharp edges. A vendor you trust changes a workflow, a permission gets granted “just for now,” and your exposure quietly grows while everyone stays busy doing real work.
If you run a family office, you already know the feeling. A perfectly reasonable decision in one corner of the operation can create a problem in another. A private deal looks fine on paper, then liquidity gets tight because capital calls do not wait for your timing. A wire request lands late on a Friday, the right approver is traveling, and the process that usually feels smooth suddenly has sharp edges. A vendor you trust changes a workflow, a permission gets granted “just for now,” and your exposure quietly grows while everyone stays busy doing real work.
Family office risk management is simply the discipline of staying ahead of those moments. It is a repeatable way to spot risks early, size them up, put sensible controls in place, and keep an eye on them without turning a lean office into a policy factory. Below, we will explore the major risk domains that show up most often in family offices and a practical framework you can run with a small team, so you can protect wealth, operations, and reputation with fewer surprises and more confidence.
What is family office risk management
Family office risk management is the ongoing work of identifying, assessing, reducing, and monitoring risks across the whole office, including investments, operations, technology, vendors, governance, and reputation. It is a repeatable process that helps you avoid avoidable mistakes and respond faster when something unexpected happens.
Most family offices do some version of this already, even if nobody calls it that. When you add a second approver for wires, when you tighten access to investor statements, when you standardize how entities are reconciled, you are managing risk. The difference between an office that feels in control and one that feels one inbox away from a mess is whether those decisions are intentional and maintained.
It helps to think of the family office as a small enterprise that just happens to manage serious assets and sensitive information. The risk lives in the seams between entities, accounts, custodians, advisors, and systems. When those seams are handled with informal habits and heroics, risk builds quietly.
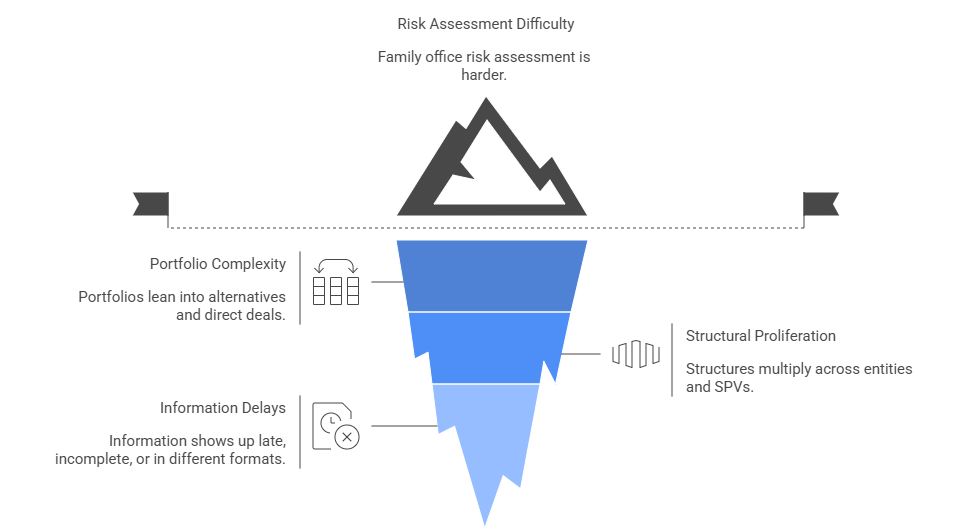
Why risk feels harder for family offices now
The day to day reality is more complicated than it used to be. Portfolios lean harder into alternatives and direct deals, structures multiply across entities and SPVs, and the information you need to understand exposure often shows up late, incomplete, or in different formats. That makes even basic family office risk assessment harder to do with confidence.
The other shift is that problems rarely stay in their lane. A process shortcut can create a fraud opening, a vendor issue can become a family office cybersecurity incident, and a governance gray area can turn a routine decision into a dispute. When the office does not have a consistent family office risk framework to connect those dots, risk tends to arrive as a surprise instead of something you saw coming.
6 core risk domains every family office should track
Most offices do not struggle because they missed a single risk. They struggle because risk is spread across a few predictable buckets, and nobody has a clean way to see them together. Tracking the same core domains year after year gives you a shared map for family office risk management, even as the people, entities, and investments change.
Investment and market risk covers what most teams think of first. Concentration, liquidity, leverage, valuation lag in alternatives, and correlations that behave nicely until they do not. The practical goal is not forecasting. It is knowing where you are exposed, where you are guessing, and what would hurt if markets move fast.
Operational risk is the stuff that breaks when a process is informal or rushed. Payment approvals, reconciliations, reporting workflows, entity management, and key person dependency all live here. This is also where spreadsheet dependency quietly turns into risk register material, especially when one file becomes the only way to understand positions, cash, or ownership.
Reduce operational risk with a unified back office
Bring accounting, investment reporting, and entity-level consolidation into one system—so controls are easier to run and maintain.
Governance and decision risk is about how choices get made and who has authority. When roles are unclear, approvals become inconsistent and disputes become more likely. Succession planning belongs here too, not as a long range concept, but as a practical control that keeps decisions and access rights from becoming ambiguous at the worst time.
Cybersecurity and privacy risk is the protection of sensitive data and the systems that hold it. Access control, MFA, least privilege, secure sharing, device hygiene, and third-party IT practices matter more in a family office because the data is valuable and the circle of trust is small. A single compromised account can create both financial loss and reputational damage in the same day.
Compliance and regulatory risk covers tax, reporting obligations, entity level requirements, and the growing expectations around documentation and transparency. The challenge is less about knowing every rule and more about avoiding blind spots when activities span jurisdictions, structures, and service providers.
Reputational and physical risk is where the stakes get personal. Public exposure, social engineering, extortion scenarios, travel security, and sensitive relationships can all land here. The key point is that reputation and personal safety are not separate from operations and cyber. They are often downstream of a control gap somewhere else.
Investment risk in a world of alternatives and direct deals
Alternatives and direct deals do not just add complexity. They change the timing and quality of the information you rely on, which makes family office risk assessment harder even when the underlying assets are solid. You are often working with valuation lag, uneven reporting, and exposures that do not show up cleanly until after decisions have already been made.
The pressure point is usually liquidity. Commitments, capital calls, and delayed distributions can turn a portfolio that looks healthy into a near term cash problem, which then spills into operational risk through rushed approvals and last minute funding moves. Concentration is another common surprise. Deals may look diversified by label, but share the same underlying drivers when stress hits.
A practical way to manage this is to be clear about what you need to know in advance and what you can only confirm later. For most teams, simple scenario planning and a consistent review rhythm do more than complex models. You are trying to avoid false confidence and keep investment risk management for family offices grounded in what the office can actually see and control.
Operational controls that prevent expensive mistakes
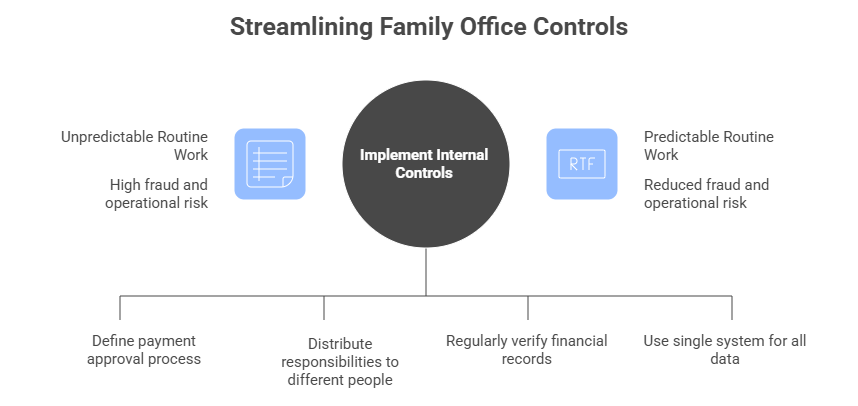
Most operational failures are boring in the worst way. A payment gets approved too quickly, a reconciliation slips, someone shares a file the easy way instead of the safe way, and the office only realizes there is a problem when money or trust is already gone. Operational risk in family offices usually comes from routine work done under time pressure, not from dramatic one off events.
The goal of internal controls for family offices is to make the routine work predictable. Clear approval rules for payments, basic separation of duties, and reconciliations that happen consistently do more to reduce fraud risk management family office exposure than any complicated policy binder. The same logic applies to vendors and advisors, because informal handoffs and broad access create gaps that nobody sees until a process breaks. Some family offices reduce operational and reporting risk by consolidating multi-entity accounting, investment activity, and audit trails in a single system, such as FundCount, so controls sit inside the workflow rather than in side files and memory. When the entity structure, transactions, and supporting documentation live together, it is easier to enforce access rules, trace who did what and when, and produce consistent reporting without rebuilding the story in spreadsheets every month.
Spreadsheets are often where this risk hides. They can be useful for analysis, but they are fragile as a system of record, especially across multiple entities.
Operational controls that prevent expensive mistakes
Most operational failures are painfully ordinary. A wire goes out with the wrong context, a reconciliation slips a week, someone shares a file the fast way instead of the safe way, and the office only learns there is a problem after money or credibility has already taken a hit.
Good internal controls for family offices keep routine work from turning into a fire drill. Clear payment approval rules, separation of duties where it matters, and consistent reconciliations shrink fraud risk management family office exposure because there are fewer gaps to exploit and fewer judgment calls under pressure. Some offices also reduce operational and reporting risk by consolidating multi entity accounting, investment activity, and audit trails in one system such as FundCount, so the controls live inside the workflow instead of in side spreadsheets and institutional memory. When the entity structure, transactions, and supporting documentation are connected, it is easier to limit access, trace who did what and when, and produce consistent reporting without rebuilding the story every month.
Spreadsheets still have a place for analysis, but they get risky when they become the system of record. That is usually when operational risk in family offices starts to hide in quiet places, right up until the day it shows up as a very loud problem.
Cybersecurity and privacy
Family offices are high value targets with unusually sensitive data, and the risk is not theoretical. One industry study cited in FundCount reporting found that 26 percent of family offices have already experienced a cyberattack, which is enough to justify treating family office cybersecurity as a core operating concern, not an IT side project.
The most effective controls are the unglamorous ones that remove easy paths. Multi factor authentication, tight role based access, and least privilege reduce the odds that a single compromised account turns into broad access across entities and documents. Encryption and audit trails matter here for a practical reason. When you can trace who accessed or changed what and when, you can contain an incident faster and answer hard questions without guessing.
Privacy risk often shows up through normal collaboration. Emailing statements, sending tax files over consumer file sharing tools, or giving vendors broad access because it is convenient are common ways sensitive information leaks. A more durable approach is to standardize secure sharing and keep access time bound and reviewable, especially for third parties who touch payments, reporting, or identity documents.
Finally, treat incident readiness as part of the control set, not an emergency task you will handle later. A simple plan that names who gets called, what gets locked down first, and how you verify payment requests when systems are under stress is often the difference between a contained event and a long, expensive week.
Governance, succession, and reputational risk
A lot of the risk in a family office is not technical or financial. It is human. When decision rights are unclear, when approvals depend on who is available, or when sensitive topics get handled through side conversations, the office ends up carrying governance risk that shows up as delays, second guessing, and occasionally real conflict.
Good governance is not about creating a boardroom inside a family. It is about making authority clear enough that the office can move quickly without guessing. Who can approve which investments, who can move cash under what conditions, what requires a second sign off, and how exceptions get documented all reduce decision risk before it becomes an argument. This is also where next gen stakeholders often care most because clarity supports trust, visibility, and reporting confidence.
Succession risk is part of the same picture. Key person dependency is not only an operational issue. When institutional knowledge, access, and relationships sit with one person, the office inherits a fragile point of failure. Succession planning is a practical control that spreads that knowledge, documents the critical workflows, and makes access rights deliberate rather than inherited by whoever is left standing.
Reputational risk in a family office tends to arrive through ordinary channels. A leaked document, a compromised inbox, an advisor who forwards something to the wrong person, or a rushed response to a sensitive situation can create lasting damage. It helps to treat reputation as something you protect with controls, not something you defend with statements after the fact. Strong privacy practices, disciplined communications, and clean records of decisions and approvals reduce the chance that the office is forced to explain what it cannot prove.
90-day implementation plan (start small, then mature)
The fastest way to make risk management stick is to start with what you can see and control, then build structure as the team gains rhythm. In the first couple of weeks, focus on a quick inventory of the most material exposures across investments, operations, cybersecurity, governance, compliance, and reputation, then agree on the top risks that truly deserve attention. This is also the point where decision rights and escalation paths need to be unambiguous, because a framework with no authority behind it turns into documentation.
Over the next month, turn that inventory into a working risk register with clear owners, simple scoring, and a short list of controls that remove obvious failure points, especially around payments, approvals, access, and reconciliations. Draft a basic incident plan so you are not inventing a response under pressure, and align vendors on how access and handoffs will work in practice.
In the final stretch, tighten reporting integrity, review vendor access and critical contracts, and run a tabletop exercise that tests a realistic scenario such as a wire fraud attempt or account compromise. By the end of 90 days, you should have a family office risk framework that is alive, owned, and reviewable, plus a cadence that keeps family office risk management from fading back into good intentions.
Common pitfalls
“We have policies, but nobody owns them.”
This is what happens when a policy gets written during a calm week, then the office goes back to running at full speed. Exceptions pile up, nobody wants to be the bottleneck, and the policy turns into a document you reference when something goes wrong. The fix is simple and unglamorous. Put one name next to each policy and make the job small. Keep it current, track exceptions, bring the messy ones back for a quick decision.
“Everything depends on one spreadsheet and one person.”
It usually starts as someone being helpful. They build a spreadsheet that ties everything together and saves the day month after month. Then that file becomes the only place the office can see exposure, cash, or entity activity in one view. When it breaks or the person is out, the office goes blind. The fix is to treat that spreadsheet like a single point of failure. Reduce what depends on it, move the core record keeping into a system that others can operate, and document the handful of steps that cannot live only in someone’s head.
“We bought tools but didn’t change process.”
This is the classic two track reality. You have a platform for reporting, but the team still rebuilds the monthly pack manually because it feels faster. You have secure sharing, but files still get emailed because that is what people default to. Nothing improves because the old way is still the real way. The fix is to pick a few workflows that matter, payments and reporting are usually good candidates, and make the new process the only process. Keep it narrow at first so the change sticks.
“We focus on one risk (cyber) and miss cross-domain exposure.”
It is easy to pour attention into the loudest risk, especially when cybersecurity is on everyone’s mind. But the real damage often comes from the seams. A social engineering attempt succeeds because payment approvals are loose. A vendor gets too much access because onboarding is informal. A sensitive decision becomes a reputational issue because governance and documentation were fuzzy. The fix is to review risks together, not in silos, so you can see how one control gap creates multiple exposures.
Conclusion
Family office risk management is not about eliminating risk. It is about making the risk you do take visible, owned, and controlled so the office is not forced to improvise under pressure. When you track the core domains together, run a simple risk framework on a predictable cadence, and tighten the operational basics that move money and data, you end up with fewer surprises and faster decisions when something does go wrong.
Family office risk management FAQ
What is family office risk management?
Family office risk management is a repeatable process to identify, assess, mitigate, and monitor risks across investments, operations, cybersecurity, governance, compliance, and reputation. The goal is to reduce avoidable losses and keep decision making steady even when conditions change.
What are the biggest risks for family offices today?
The biggest risks usually cluster around investment complexity, operational errors, cybersecurity and privacy exposure, governance ambiguity, and compliance blind spots. What makes them dangerous is how often they connect, like a vendor issue turning into a cyber incident or a process shortcut opening the door to fraud.
What does a risk framework look like for a small team?
For a small team, a family office risk framework is a simple operating rhythm with clear decision rights, a living risk register with owners, a basic scoring method, and a consistent review cadence. It should fit inside regular meetings and workflows, not require a separate bureaucracy to maintain.
How do you reduce fraud and payment risk?
You reduce fraud and payment risk by tightening approvals, separating duties where possible, and making reconciliations consistent and timely. The practical goal is to prevent rushed exceptions and to make verification the default, especially for changes in payee details, urgent requests, and anything initiated over email.
How can technology reduce operational risk?
Technology reduces operational risk by standardizing workflows, limiting access appropriately, and preserving audit trails so the office can trace activity without guesswork. It also reduces key person dependency when multi entity data, transactions, and reporting live in one controlled system rather than scattered spreadsheets and side files.







